Netgear UTM25-100NAS Reference Manual - Page 299
Configuring User, Group, and Global Policies, Apply, delete
 |
UPC - 606449061383
View all Netgear UTM25-100NAS manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 299 highlights
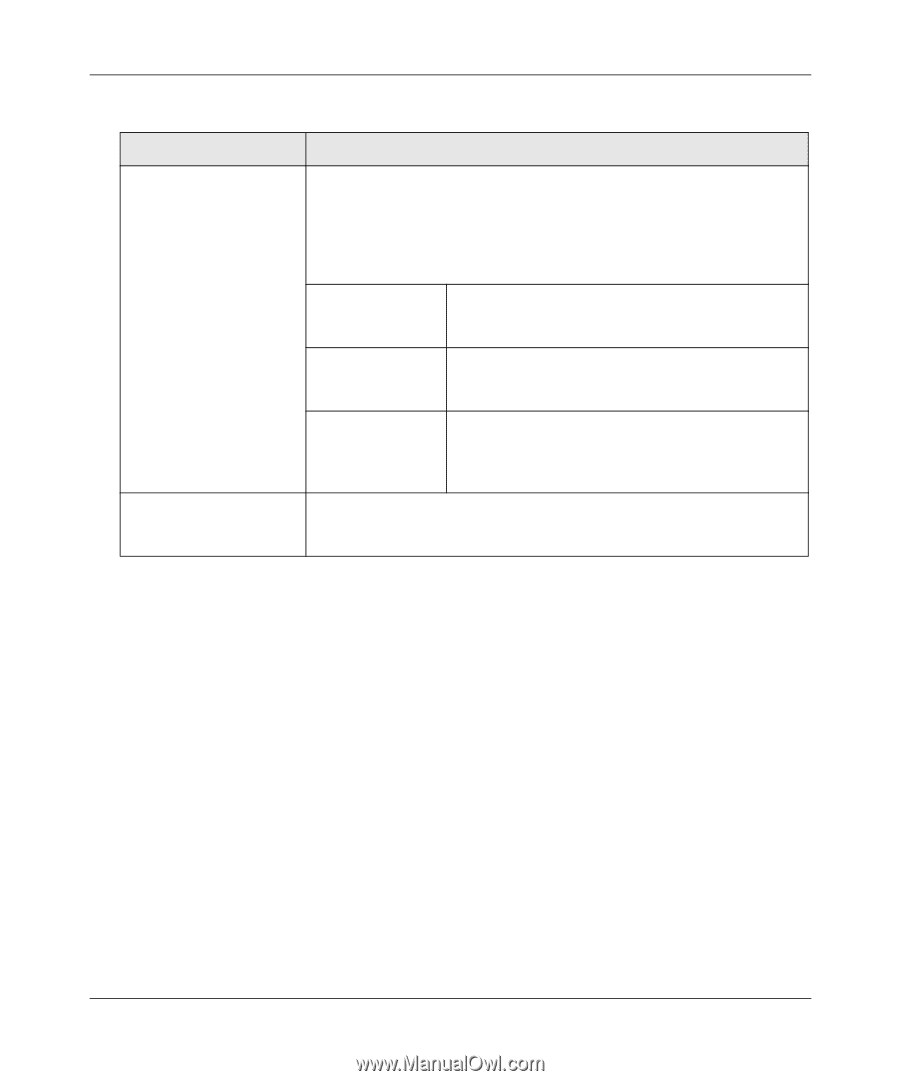
ProSecure Unified Threat Management UTM10 or UTM25 Reference Manual Table 8-9. Add Resource Addresses Settings (continued) Item Description (or Subfield and Description) Object Type From the pull-down menu, select one of the following options: • IP Address. The object is an IP address. You must enter the IP address or the FQDN in the IP Address / Name field. • IP Network. The object is an IP network, You must enter the network IP address in the Network Address field and the network mask length in the Mask Length field. IP Address / Name Applicable only when you select IP Address as the Object Type: enter the IP address or FQDN for the location that is permitted to use this resource. Network Address Applicable only when you select IP Network as the Object Type: enter the network IP address for the locations that are permitted to use this resource. Mask Length Applicable only when you select IP Network as the Object Type: as an option, enter the network mask (0-31) for the locations that are permitted to use this resource. Port Range / Port Number A port or a range of ports (0-65535) to apply the policy to; the policy is applied to all TCP and UDP traffic that passes on those ports. Leave the fields blank to apply the policy to all traffic. 5. Click Apply to save your settings. The new configuration is added to the Defined Resource Addresses table. To delete a configuration from the Defined Resource Addresses table, click the delete table button to the right of the configuration that you want to delete. Configuring User, Group, and Global Policies You can define and apply user, group and global policies to predefined network resource objects, IP addresses, address ranges, or all IP addresses and to different SSL VPN services. A specific hierarchy is invoked over which policies take precedence. The UTM policy hierarchy is defined as: 1. User policies take precedence over all group policies. 2. Group policies take precedence over all global policies. 3. If two or more user, group or global policies are configured, the most specific policy takes precedence. Virtual Private Networking Using SSL Connections v1.0, September 2009 8-31